SoftwarePlaza IT Magazine
Login to your Account
Create Affiliate Account
Trouble Signing In?
Enter your email below to request a Reset Password Link
-
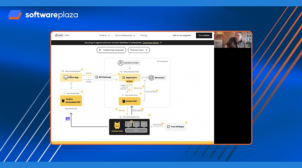
How Cerbos Uses Zero-Trust to Defend Against Non-Human Identity (NHI) Threats
Learn how Cerbos secures non-human identities with real-time, zero-trust authorization and a stateless, standards-based approach.
-
8 Capabilities of JFrog that can enhance Security and Compliance Throughout the SDLC
JFrog features to improve security and compliance across SDLC—from artifact traceability to policy enforcement and continuous scanning.
-
3 ways Sweet Security reduces cloud MTTR by 90%
Read about the main reasons why Sweet Security is the right chose to reduce MTTR and secure cloud workloads.
-
Third‑Party Software Breach Puts NHS Devices and Possibly Patient Records at Risk
Sensitive NHS data at risk after a cyberattack exploits a mobile software flaw, affecting two major UK hospitals and prompting a national investigation.
-
Choosing the Right Cybersecurity Framework: NIST, ISO 27001, CIS, or Zero Trust
Learn how to choose the right cybersecurity framework: NIST, ISO 27001, CIS Controls, or Zero Trust, based on your company’s size, risk, and maturity.
-
10 Practical Approaches for Cost Optimization in Hybrid Cloud Environments
Cut hybrid cloud costs with 10 proven strategies for visibility, scaling, and smarter compute—all without sacrificing performance or agility.
-
Is End-to-End Encryption Replacing Traditional Cryptographic Models?
Is end-to-end encryption replacing traditional cryptography? Explore why evolving tech demands new models like E2EE, ZKPs, and post-quantum security.
-
Legal Aid Agency Hit by Major Cyberattack
A cyberattack on the Legal Aid Agency has exposed data from 2010, and the MoJ is warning and acting fast.
-
BERT Ransomware Shuts Down ESXi Virtual Machines to Block Recovery
BERT ransomware shuts down VMware ESXi virtual machines before encryption, blocking recovery efforts and targeting hybrid IT environments across continents.
-
10 Benefits of Integrating Agentic AI in Cloud-Native Infrastructures: A Deep Dive with Solo.io
Discover how Agentic AI and Solo.io transform cloud-native automation—enabling smarter decision-making, self-healing systems, and cost-optimized performance
-
NVIDIA and Google Cloud Unveil Game-Changing AI Innovations Around Gemini, Blackwell, and More
NVIDIA and Google Cloud launch new AI innovations for Gemini, Blackwell GPUs, and secure cloud workloads to empower developers and enterprises.
-
SAP and Microsoft Launch Joint Program to Accelerate Cloud ERP Adoption
Modernise ERP with AI-driven agents, cloud-grade reliability, and partner-led adoption via SAP’s new program on Microsoft Cloud.