SoftwarePlaza IT Magazine
Login to your Account
Create Affiliate Account
Trouble Signing In?
Enter your email below to request a Reset Password Link
-
U.S. Department of Energy Partners with AMD in $1 Billion Supercomputing and AI Infrastructure Initiative
The U.S. Department of Energy and AMD launch a $1 billion partnership to build next-generation supercomputers, advancing America’s leadership in AI, energy, and scientific innovation.
-
Understand CloudBolt's Orchestration-First Approach To Remove 'Report Factory' In FinOps
Read about CloudBolt’s take on removing ‘report factory’ in FinOps using an orchestration-first approach.
-
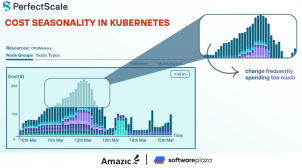
Understanding Cost Seasonality in Kubernetes
Unpack the concept of cost seasonality in Kubernetes, explore the factors that drive its fluctuations, and discover effective strategies—including right-sizing, autoscaling optimization, and leveraging tools like PerfectScale—to manage and predict your cloud spend while maintaining performance.
-
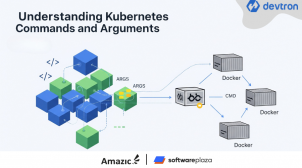
Understanding Kubernetes Commands and Arguments
Want to customize what runs inside your Kubernetes containers? This blog shows you how to use commands and arguments to override Docker defaults, with practical examples and use cases like running startup scripts and testing network connectivity.
-
Understanding SBOM Software: The Foundation of Modern Cybersecurity
A Software Bill of Materials (SBOM) is the key to understanding what’s inside your software—and securing it. This article explores the growing importance of SBOMs in cybersecurity, the difference between static and dynamic SBOMs, how AI is transforming their effectiveness, and best practices for managing software supply chain risk.
-
Unifying the Cloud with HashiCorp: Developer Favorites, HCP Insights & KubeCon Highlights
Melissa Gurney of HashiCorp shares her DevRel journey, explores HCP’s impact, and highlights why developers rely on Terraform, Vault, and Consul—live from KubeCon.
-
Unlimited access to Docker Hardened Images: Because security should be affordable, always
The cost of security shouldn't limit protection. Docker now offers unlimited access to its Hardened Images (DHI) catalog via an affordable subscription. Get near-zero CVEs, a 95% smaller attack surface, and SRLabs-validated security with SBOM/VEX support for every team, from ML workloads to FedRAMP-ready environments.
-
Unlocking Kubernetes at Scale: Insights from Mirantis
Dominic Wilde of Mirantis discusses Kubernetes adoption challenges, introduces k0rdent for simplified operations, and shares Mirantis’ key KubeCon message and future vision in this exclusive interview.
-
Unmasking Shadow AI: Witness AI & Network Observability for the Era of Agentic AI
Explore how network-based observability helps enterprises tackle agent-based and shadow AI risks. Trevor Welsh of Witness AI shares insights on securing sensitive data and enforcing AI policies.
-
Use Of Open Source IT Monitoring Tools in 2025
A deep dive into popular open-source monitoring tools like Prometheus and Grafana and how to use them risk-free
-
Valuable insights for organizations navigating NIS2 compliance
Discover valuable insights for navigating NIS2 compliance, from expanded scope and stricter security requirements to increased accountability.
-
Venom Spider Targets HR Departments With Sophisticated Resume Scam
Cybersecurity experts at Arctic Wolf Labs uncover a new phishing campaign where fake resumes hide the advanced More_eggs backdoor malware, targeting corporate HR teams.