SoftwarePlaza IT Magazine
Login to your Account
Create Affiliate Account
Trouble Signing In?
Enter your email below to request a Reset Password Link
-
How Teleport’s Identity-Aware Access Model Reinvents Zero-Trust for Multicloud Kubernetes
Implementing zero trust in multicloud setups using workload identities, service meshes, policy-as-code, and Teleport’s identity-based access model.
-
How Observability Data Lakes Enable Real-Time Operational Insights
Discover how observability data lakes unify telemetry, reduce MTTR, and enable AI-driven, real-time operational insights for proactive and predictive operations.
-
How Snyk’s New Container Intelligence Improves FinOps Outcomes for Kubernetes and Serverless
Learn how Snyk’s container intelligence helps FinOps teams optimize Kubernetes and serverless costs through smarter security, rightsizing, and CI/CD integration.
-
Modern API Security: Infinidat’s Approach to Detecting Risks in Cloud-Native Apps
Modern API security explained: why APIs are prime targets, common OWASP risks, runtime protection, AI anomaly detection, and secure-by-default cloud-native design.
-
Lightweight Edge Kubernetes for IoT in Retail & Manufacturing
From factories to remote sites, running Kubernetes at the edge with k3s and MicroK8s under real IoT constraints.
-
How to Achieve Real-Time Visibility with Upwind’s eBPF-Powered Platform
Achieve real-time cloud security with Upwind’s eBPF-powered platform. Learn how runtime visibility reduces noise, stops exploits, and protects AI and Kubernetes workloads.
-
9 Facts You Need to Know About SpiceDB’s Relationship-Based Access Control
Discover how SpiceDB uses ReBAC, low-latency architecture, and centralized authorization to deliver scalable, flexible, and AI-ready access control for modern apps.
-
4 insights into AI, compliance, and modern infrastructure in financial services
Insights into AI adoption, compliance challenges, and modern infrastructure trends shaping financial services, with lessons from real-world transformation.
-
How Beagle Security Helps Organizations Move Beyond Vulnerability Scanners
Discover why traditional scanners fall short and how Beagle Security enables continuous, API-focused testing for faster, stronger application security.
-
10 Things You Need to Know About install4j, The Powerful Multi-Platform Java Installer Builder
Discover why install4j is one of the most reliable multi-platform Java installer builders: features, real-world benefits, and what to know before choosing it.
-
7 Ways AI is Transforming Threat Detection and Cyber Defense
Explore 7 ways AI is reshaping threat detection and cyber defense, from predictive intelligence to adaptive protection for modern security teams.
-
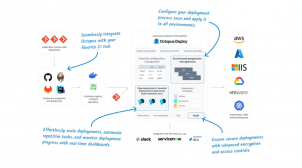
How Octopus Helps Implement Security and Operational Policies for Healthier Platform Adoption
Discover how Octopus Deploy automates security and operational policies to drive healthier, compliant, and developer-friendly platform adoption.