SoftwarePlaza IT Magazine
Login to your Account
Create Affiliate Account
Trouble Signing In?
Enter your email below to request a Reset Password Link
-
How Arnica Is Redefining Application Security by Winning the Heart of Developers
Discover how Arnica is reshaping application security with AI-driven insights, developer-first workflows, Git-based automation, and proactive vulnerability reduction, shared by CEO Nir Valtman in action.
-
From DevOps to Platforms: How Krumware thinks about real Platform Engineering
Colin Griffin of Krumware discusses platform engineering beyond DevOps, treating platforms as products, culture and UX, pitfalls, and lessons with the CNCF Platforms White Paper.
-
Secure Blink on Fixing What’s Broken in Application & API Security
Explore how AI transforms application and API security as Secure Blink co-founder Sonal Khanna discusses THREATSPY, developer-first security, reachability prioritization, recognition, and future-ready API teams.
-
Redefining Enterprise Storage with Infinidat
Eric Herzog reveals how Infinidat revolutionizes enterprise storage with performance, resilience, simplicity, cyber-storage, AI automation, and scalable reliability to solve modern IT challenges for organizations.
-
Global Surge in IoT Devices Signals a New Era for Connected Intelligence
IoT devices will rise 14% to 21.1 billion this year. We explore how Wi-Fi, Bluetooth, and cellular IoT are driving global growth and enabling the next wave of edge intelligence.
-
Latest Updates in Data Privacy and Governance Laws Around the World in 2025
Explore the latest 2025 data privacy and AI governance laws across regions and understand what future regulations mean for your business and digital strategy.
-
Microsoft Blocks Record 15.72 Tbps DDoS Attack From Expanding AISURU Botnet
Microsoft mitigated a record 15.72 Tbps DDoS attack launched by the AISURU botnet, revealing rising IoT-driven threats and growing risks to cloud services.
-
Rush Street Interactive Levels Up Cloud Security with Teleport
Rush Street Interactive strengthened its multi-cloud security by adopting Teleport’s unified access platform, replacing SSH keys and VPN friction with short-lived credentials, SSO, RBAC, and reverse tunnels. The result: faster onboarding, reduced attack surface, streamlined compliance, and highly secure access for both engineers and automation workflows.
-
How IBM Instana uses Teleport to manage access to their cloud infrastructure
IBM Instana needed to secure access to its sensitive cloud infrastructure while boosting developer agility. Discover why they chose Teleport to replace VPNs and shared credentials, simplifying compliance audits (SOC 2, FedRAMP) and eliminating management overhead across their rapidly scaling, multi-cloud environment.
-
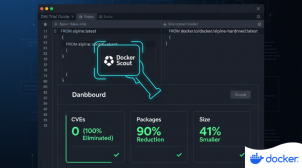
Making the Most of Your Docker Hardened Images Trial – Part 1
Start your DHI trial strong! This guide shows how Docker Hardened Images move you to near-zero CVEs in 3 steps. We compared official Node.js to DHI and found a 100% vulnerability elimination (25 CVEs to 0), a 90% package reduction, and 41% smaller images, validating the compliance benefits with Docker Scout and SBOMs.
-
Unlimited access to Docker Hardened Images: Because security should be affordable, always
The cost of security shouldn't limit protection. Docker now offers unlimited access to its Hardened Images (DHI) catalog via an affordable subscription. Get near-zero CVEs, a 95% smaller attack surface, and SRLabs-validated security with SBOM/VEX support for every team, from ML workloads to FedRAMP-ready environments.
-
Expanding Docker Hardened Images: Secure Helm Charts for Deployments
Docker is simplifying Kubernetes security! Discover how new Helm charts in the Docker Hardened Images (DHI) Catalog give users a secure, compliance-ready alternative after the Broadcom/Bitnami changes. Deploy DHI by default, ensuring SLSA Level 3 security and SLA-backed patching for every Kubernetes workload.