Login to your Account
Create Affiliate Account
Trouble Signing In?
Enter your email below to request a Reset Password Link
-
7 Ways AI is Transforming Threat Detection and Cyber Defense
Explore 7 ways AI is reshaping threat detection and cyber defense, from predictive intelligence to adaptive protection for modern security teams.
-
How Octopus Helps Implement Security and Operational Policies for Healthier Platform Adoption
Discover how Octopus Deploy automates security and operational policies to drive healthier, compliant, and developer-friendly platform adoption.
-
How GitKraken MCP Uses AI to Supercharge Your Dev Workflow
GitKraken MCP uses AI and real project context to cut friction, reduce tool switching and turn your coding assistant into a true development teammate.
-
How Formae is Transforming Platform Engineering by Replacing Brittle YAML/JSON
Formae transforms platform engineering with codification, replacing brittle YAML and JSON to create safer, faster infrastructure workflows.
-
7 Ways PointFive Automates Daily Cloud Operations for Efficiency and Scale
Explore seven ways PointFive automates daily cloud operations to cut waste, improve reliability, and scale faster.
-
Check Point Unveils ThreatCloud NextGen: AI-Powered Threat Intelligence for Real-Time Attack Prevention
Check Point unveils ThreatCloud NextGen, an AI-powered threat intelligence platform delivering real-time cyberattack prediction and prevention for modern enterprises.
-
How to Automate API Security with SecureBlink
Automate API security effortlessly with SecureBlink and protect your applications with continuous monitoring and smart vulnerability remediation.
-
Rush Street Interactive Levels Up Cloud Security with Teleport
Rush Street Interactive strengthened its multi-cloud security by adopting Teleport’s unified access platform, replacing SSH keys and VPN friction with short-lived credentials, SSO, RBAC, and reverse tunnels. The result: faster onboarding, reduced attack surface, streamlined compliance, and highly secure access for both engineers and automation workflows.
-
How IBM Instana uses Teleport to manage access to their cloud infrastructure
IBM Instana needed to secure access to its sensitive cloud infrastructure while boosting developer agility. Discover why they chose Teleport to replace VPNs and shared credentials, simplifying compliance audits (SOC 2, FedRAMP) and eliminating management overhead across their rapidly scaling, multi-cloud environment.
-
Reimagining Observability: How Splunk is Powering the Future with OpenTelemetry
Discover how Splunk’s Steve Flanders drives innovation in observability through OpenTelemetry, enabling vendor-neutral telemetry, scalable data pipelines, and AI-driven insights for cloud-native system reliability.
-
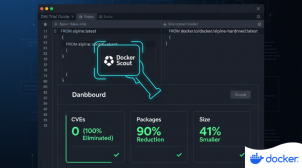
Making the Most of Your Docker Hardened Images Trial – Part 1
Start your DHI trial strong! This guide shows how Docker Hardened Images move you to near-zero CVEs in 3 steps. We compared official Node.js to DHI and found a 100% vulnerability elimination (25 CVEs to 0), a 90% package reduction, and 41% smaller images, validating the compliance benefits with Docker Scout and SBOMs.
-
Unlimited access to Docker Hardened Images: Because security should be affordable, always
The cost of security shouldn't limit protection. Docker now offers unlimited access to its Hardened Images (DHI) catalog via an affordable subscription. Get near-zero CVEs, a 95% smaller attack surface, and SRLabs-validated security with SBOM/VEX support for every team, from ML workloads to FedRAMP-ready environments.