Login to your Account
Create Affiliate Account
Trouble Signing In?
Enter your email below to request a Reset Password Link
-
How Internal Developer Platforms integrate the DevOps pipeline end-to-end
Learn how IDPs create a cohesive, efficient DevOps pipeline that enhances collaboration, improves software quality, and accelerates delivery times.
-
How MariaDB Is Redefining Database Security in the Zero-Trust Era
MariaDB helps businesses to redefine their database security in the zero-trust era by providing advanced features like encryption, granular access control, and continuous auditing to verify every request and secure data from internal and external threats.
-
How Nutanix helps architect & manage hyperconverged cloud infrastructure
Simplify multi-cloud management with Nutanix HCI. Discover how it streamlines operations, boosts security, cuts costs, and prepares businesses for future tech.
-
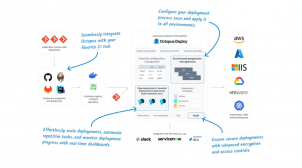
How Octopus Helps Implement Security and Operational Policies for Healthier Platform Adoption
Discover how Octopus Deploy automates security and operational policies to drive healthier, compliant, and developer-friendly platform adoption.
-
How Spacelift Can Improve Your Infrastructure Orchestration
Discover how Spacelift enhances infrastructure orchestration by streamlining complex workflows, improving governance, and increasing developer velocity. This guide covers Spacelift’s key features—from automated IaC workflows and policy-based access control to drift detection, resource visualization, and self-service infrastructure. Learn how Spacelift helps platform and DevOps teams manage Terraform, Pulumi, Kubernetes, and more with robust security, flexibility, and scalability.
-
How Sweet Security’s Issues Hub Streamlines Cloud Risk Management Across Teams
Sweet Security’s Issues Hub helps teams detect, prioritize, and resolve cloud threats by correlating risks across workloads, secrets, and identities.
-
How Teleport addresses infrastructure security identity issues and policy challenges
Read to learn how Teleport tackles infrastructure security identity issues and policy challenges in the ever-changing IT landscape.
-
How to leverage S3 in a world of AI/ML workloads while also focusing on scalability
Learn how to leverage AWS S3 for scalable, secure storage of AI/ML workloads, ensuring performance, cost efficiency, and seamless data management.
-
How to Mitigate Risks in Global Supply Chains
The worldwide supply chain is a complex web of interconnected networks, supported by a range of global supply chain services that keep goods flowing across bord
-
How to Overcome Performance Issues in Java with JProfiler
Learn how JProfiler helps deal with issues like memory leaks, thread contention, CPU bottlenecks, and more.
-
How to Turn Your SBOM Into a Supply Chain Security Powerhouse with Anchore
Turn SBOMs into a security advantage with Anchore’s Bring Your Own SBOM, Anchore Rank, and automation to boost supply chain visibility and risk management.
-
How To Use Machine Learning To Reduce Human Error in CI/CD Pipelines With GitLab
Learn about how machine learning can enhance CI/CD processes and all the ways GitLab can make it flawless