Login to your Account
Create Affiliate Account
Trouble Signing In?
Enter your email below to request a Reset Password Link
-
How Beagle Security Helps Organizations Move Beyond Vulnerability Scanners
Discover why traditional scanners fall short and how Beagle Security enables continuous, API-focused testing for faster, stronger application security.
-
10 Things You Need to Know About install4j, The Powerful Multi-Platform Java Installer Builder
Discover why install4j is one of the most reliable multi-platform Java installer builders: features, real-world benefits, and what to know before choosing it.
-
Shaping the Future of Documentation: Taylor Dolezal on OSS, Knowledge & Dosu.dev
Taylor Dolezal of Dosu.dev explores living documentation, open-source roots, AI-driven, context-aware knowledge, and Dosu’s fact-and-citation approach to unify fragmented tools for maintainers and enterprises alike.
-
Inside Modern Infra: Kerim Satirli on Terraform, Vault Radar & AI-Safe Workflows
Kerim Satirli returns to unpack HashiCorp’s latest: Terraform Stacks, Actions, Search, Infragraph, and Vault Radar, plus AI-agent rise and supply-chain threats like Shi Hulud attack.
-
7 Ways AI is Transforming Threat Detection and Cyber Defense
Explore 7 ways AI is reshaping threat detection and cyber defense, from predictive intelligence to adaptive protection for modern security teams.
-
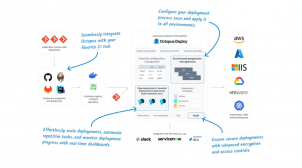
How Octopus Helps Implement Security and Operational Policies for Healthier Platform Adoption
Discover how Octopus Deploy automates security and operational policies to drive healthier, compliant, and developer-friendly platform adoption.
-
How GitKraken MCP Uses AI to Supercharge Your Dev Workflow
GitKraken MCP uses AI and real project context to cut friction, reduce tool switching and turn your coding assistant into a true development teammate.
-
How Formae is Transforming Platform Engineering by Replacing Brittle YAML/JSON
Formae transforms platform engineering with codification, replacing brittle YAML and JSON to create safer, faster infrastructure workflows.
-
7 Ways PointFive Automates Daily Cloud Operations for Efficiency and Scale
Explore seven ways PointFive automates daily cloud operations to cut waste, improve reliability, and scale faster.
-
Check Point Unveils ThreatCloud NextGen: AI-Powered Threat Intelligence for Real-Time Attack Prevention
Check Point unveils ThreatCloud NextGen, an AI-powered threat intelligence platform delivering real-time cyberattack prediction and prevention for modern enterprises.
-
How to Automate API Security with SecureBlink
Automate API security effortlessly with SecureBlink and protect your applications with continuous monitoring and smart vulnerability remediation.
-
How IBM Instana uses Teleport to manage access to their cloud infrastructure
IBM Instana needed to secure access to its sensitive cloud infrastructure while boosting developer agility. Discover why they chose Teleport to replace VPNs and shared credentials, simplifying compliance audits (SOC 2, FedRAMP) and eliminating management overhead across their rapidly scaling, multi-cloud environment.