Login to your Account
Create Affiliate Account
Trouble Signing In?
Enter your email below to request a Reset Password Link
-
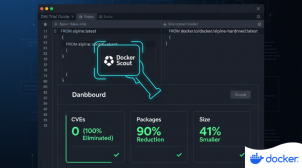
Making the Most of Your Docker Hardened Images Trial – Part 1
Start your DHI trial strong! This guide shows how Docker Hardened Images move you to near-zero CVEs in 3 steps. We compared official Node.js to DHI and found a 100% vulnerability elimination (25 CVEs to 0), a 90% package reduction, and 41% smaller images, validating the compliance benefits with Docker Scout and SBOMs.
-
Unlimited access to Docker Hardened Images: Because security should be affordable, always
The cost of security shouldn't limit protection. Docker now offers unlimited access to its Hardened Images (DHI) catalog via an affordable subscription. Get near-zero CVEs, a 95% smaller attack surface, and SRLabs-validated security with SBOM/VEX support for every team, from ML workloads to FedRAMP-ready environments.
-
Expanding Docker Hardened Images: Secure Helm Charts for Deployments
Docker is simplifying Kubernetes security! Discover how new Helm charts in the Docker Hardened Images (DHI) Catalog give users a secure, compliance-ready alternative after the Broadcom/Bitnami changes. Deploy DHI by default, ensuring SLSA Level 3 security and SLA-backed patching for every Kubernetes workload.
-
Docker Hardened Images: crafted by humans, protected by AI
Docker’s Hardened Images (DHI) are secured by a dual approach: human expertise backed by AI. Discover how Docker’s internal AI guardrail spotted a critical logic flaw in an nginx-exporter update, blocked the release, and contributed the fix upstream, proving AI is the best force multiplier for security architects
-
Turning Migration Into a Strategic Advantage
For fintechs, trust depends on uptime — every transaction must work flawlessly. This article explores how financial technology companies can migrate to AWS without downtime, protecting both performance and reputation. Discover resilience-first strategies like automation, blue/green deployments, and compliance-by-design that turn cloud migration into a strategic advantage rather than a risk.
-
Information sent using unencrypted channels
Information sent using unencrypted channels refers to data transmitted over a network without encryption, making it vulnerable to interception, modification, or unauthorized access.
-
How to Use Grafana for Cost Optimization and Kubernetes Observability
Explore how Grafana is used for Kubernetes observability, including best practices, custom Grafaana dashboard features and more.
-
Latest GDPR 2.0 and AI Act updates to battle AI-driven data privacy risks
Explore GDPR 2.0 and the AI Act updates, new compliance rules, and strategies to keep your AI apps privacy-compliant.
-
10 ways to manage IoT workloads on lightweight Kubernetes clusters with Portainer
Simplify IoT workload management on lightweight Kubernetes clusters with Portainer. Discover 10 ways to deploy, secure, and easily scale your edge devices.
-
What is Sustainable Data Management and How Can Companies Reduce Their Carbon Footprints
Understand sustainable data management and its effects on reducing carbon footprints for digitally-driven businesses.
-
10 AI-driven cyber threats targeting cloud environments and how to overcome them using Sysdig
Protect your cloud from AI-driven threats! Discover the top 10 attack vectors and learn how Sysdig helps detect, prevent, and neutralize evolving cyber risks.
-
How To Use Machine Learning To Reduce Human Error in CI/CD Pipelines With GitLab
Learn about how machine learning can enhance CI/CD processes and all the ways GitLab can make it flawless