Login to your Account
Create Affiliate Account
Trouble Signing In?
Enter your email below to request a Reset Password Link
-
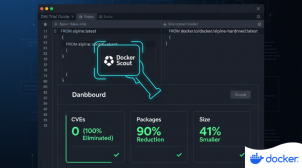
Making the Most of Your Docker Hardened Images Trial – Part 1
Start your DHI trial strong! This guide shows how Docker Hardened Images move you to near-zero CVEs in 3 steps. We compared official Node.js to DHI and found a 100% vulnerability elimination (25 CVEs to 0), a 90% package reduction, and 41% smaller images, validating the compliance benefits with Docker Scout and SBOMs.
-
How IBM Instana uses Teleport to manage access to their cloud infrastructure
IBM Instana needed to secure access to its sensitive cloud infrastructure while boosting developer agility. Discover why they chose Teleport to replace VPNs and shared credentials, simplifying compliance audits (SOC 2, FedRAMP) and eliminating management overhead across their rapidly scaling, multi-cloud environment.
-
Rush Street Interactive Levels Up Cloud Security with Teleport
Rush Street Interactive strengthened its multi-cloud security by adopting Teleport’s unified access platform, replacing SSH keys and VPN friction with short-lived credentials, SSO, RBAC, and reverse tunnels. The result: faster onboarding, reduced attack surface, streamlined compliance, and highly secure access for both engineers and automation workflows.
-
Microsoft Blocks Record 15.72 Tbps DDoS Attack From Expanding AISURU Botnet
Microsoft mitigated a record 15.72 Tbps DDoS attack launched by the AISURU botnet, revealing rising IoT-driven threats and growing risks to cloud services.
-
AI Threat Detection Tool for Modern Cyber Threats
Discover how AI threat detection transforms cybersecurity by identifying emerging threats, securing AI/ML workloads, and enabling proactive, real-time defense for cloud-native and hybrid environments.