Login to your Account
Create Affiliate Account
Trouble Signing In?
Enter your email below to request a Reset Password Link
-
PostgreSQL® extensions you need to know in 2025
Uncover the pivotal role of PostgreSQL's extensions ecosystem, its historical context, and why it remains indispensable for modern data needs, including AI and analytics. Dive into key extensions like TimescaleDB, PostGIS, and pgvector, and learn how a managed service, like Aiven, mitigates risks and enhances reliability.
-
Rails debug mode enabled
Uncover the critical security risks of running Ruby on Rails in development mode on a live server, from exposing internal workings and sensitive information to increasing the risk of remote code execution and DoS attacks. Learn practical steps to safeguard your application and prevent these vulnerabilities.
-
How to store and secure sensitive data in web applications
Given the surge in web application data breaches, learn how to effectively store and secure sensitive data in your web applications. This article explores critical data types, client-side and server-side storage mechanisms, common OWASP Top 10 vulnerabilities, and essential protective measures like robust authentication, access control, and encryption strategies.
-
Master API security: Securing your entire API ecosystem with Beagle Security’s API discovery
Discover how unchecked API sprawl creates critical security blind spots for fast-growing fintech startups, leading to data breaches and operational inefficiencies. Learn how Beagle Security's API discovery feature automatically uncovers and tests all APIs within Kubernetes or Istio environments, ensuring complete visibility and proactive vulnerability management.
-
How much does pen testing cost (2025)
Explore the true costs of penetration testing in 2025, breaking down pricing by scope (web, mobile, API, cloud, network, IoT) and methodology (black box, grey box, white box). Discover key factors influencing costs and learn how AI-powered solutions like Beagle Security offer a faster, more affordable alternative to traditional pen tests.
-
How PerfectScale Helps a DevOps Team of One Scale Riftweaver
Discover how Riftweaver, an innovative gaming studio with a one-person DevOps team, leveraged PerfectScale to reduce CPU throttling by nearly 59% in critical APIs, improve user experience, and enable efficient scaling of their AWS EKS Kubernetes environment, even on a free plan.
-
Optimizing K8s Cost to Strengthen Competitive Advantage
Discover how cybersecurity leader Cynet, with a focus on simplicity, leveraged PerfectScale to gain unprecedented visibility into pod costs, streamline Kubernetes cost optimization, and proactively identify and resolve resiliency issues across their multi-cluster AWS EKS environment, ensuring a stable and cost-effective solution for their customers.
-
Kubernetes Cost Optimization: From Roadblocks to Results
Discover how Trax, a leader in retail technology, leveraged PerfectScale to overcome manual Kubernetes optimization roadblocks, achieving an astounding 75% cost reduction in one cluster (saving over 6-figures annually) and significantly improving their "cost per processing" metric by gaining granular visibility and actionable insights across their multi-cloud, multi-cluster AWS EKS environment.
-
FinOps in 2025: The 6 Phases of FinOps Evolution
Explore the six evolving phases of FinOps, from the initial "Observational" data collection to "Automated" and the future of "Integrated FinOps," revealing how organizations learn to manage cloud spend and optimize infrastructure efficiently over time.
-
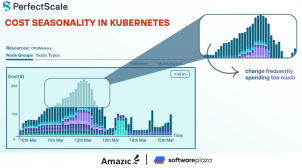
Understanding Cost Seasonality in Kubernetes
Unpack the concept of cost seasonality in Kubernetes, explore the factors that drive its fluctuations, and discover effective strategies—including right-sizing, autoscaling optimization, and leveraging tools like PerfectScale—to manage and predict your cloud spend while maintaining performance.
-
How Rapyd Solved Observability Gaps to Cut K8s Costs by 40%
Discover how fintech leader Rapyd partnered with PerfectScale to close observability gaps in their Kubernetes environment, achieving a projected 35-40% reduction in K8s costs while simultaneously improving performance and proactively resolving critical issues across their extensive AWS EKS infrastructure.
-
Is Speed Better than Security. Resolving the DevOps Dilemma with Checkmarx.
Is speed more important than security in DevOps? With Checkmarx, you don’t have to choose. Learn how AI-powered security integrates seamlessly into your workflows.