Login to your Account
Create Affiliate Account
Trouble Signing In?
Enter your email below to request a Reset Password Link
-
Latest GDPR 2.0 and AI Act updates to battle AI-driven data privacy risks
Explore GDPR 2.0 and the AI Act updates, new compliance rules, and strategies to keep your AI apps privacy-compliant.
-
Latest Updates in Data Privacy and Governance Laws Around the World in 2025
Explore the latest 2025 data privacy and AI governance laws across regions and understand what future regulations mean for your business and digital strategy.
-
Leading Global FinTech's DynamoDB Cost Optimization with PointFive
A global FinTech giant partnered with PointFive to uncover hidden inefficiencies in their DynamoDB usage. With deep waste detection and actionable recommendations, they reduced storage costs by 60% for key tables and eliminated waste from inactive data—achieving significant savings in just 10 days without slowing innovation.
-
Leading logistics company improves global DevOps efficiency and security with the JFrog platform
A global leader in advanced logistics solutions has consistently pushed the boundaries of innovation in its field, providing cutting-edge technology and devices powered by advanced inspection tools, metrology systems, and computational analytics.
-
Legal Aid Agency Hit by Major Cyberattack
A cyberattack on the Legal Aid Agency has exposed data from 2010, and the MoJ is warning and acting fast.
-
Leverage PerfectScale to Handle GPU Utilization Optimization Challenges
Boost GPU utilization without extra hardware. Learn how visibility, quick wins, smarter scheduling & PerfectScale automation cut costs & waste.
-
Leveraging Devtron for Secure CI/CD Pipelines
Devtron bakes security into CI/CD pipelines—blocking vulnerabilities, enforcing policies, and automating compliance without slowing deployments. Kubernetes-native, audit-ready, and trusted by enterprises.
-
Lightweight Edge Kubernetes for IoT in Retail & Manufacturing
From factories to remote sites, running Kubernetes at the edge with k3s and MicroK8s under real IoT constraints.
-
List of the top Ingress controllers for Kubernetes
Are you looking for a way to expose software services to external networks easily? Look no further than Ingress controllers for Kubernetes.
-
LoRaWAN Explained: Protocol, Perks, and Use Cases
Unpack LoRaWAN: the low-power, long-range protocol powering the IoT revolution! Discover its unique features, star-of-stars architecture, and diverse applications from smart cities to industrial automation. Learn how it delivers cost-effectiveness, scalability, and enhanced connectivity, and how Netmaker boosts its network security.
-
MacOS and Kubernetes: Agoda Brought Together the Traditionally Incompatible
Learn all about macOS-vz-Kubelet, Agoda’s answer to making macOS and Kubernetes work together.
-
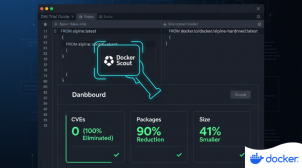
Making the Most of Your Docker Hardened Images Trial – Part 1
Start your DHI trial strong! This guide shows how Docker Hardened Images move you to near-zero CVEs in 3 steps. We compared official Node.js to DHI and found a 100% vulnerability elimination (25 CVEs to 0), a 90% package reduction, and 41% smaller images, validating the compliance benefits with Docker Scout and SBOMs.