Login to your Account
Create Affiliate Account
Trouble Signing In?
Enter your email below to request a Reset Password Link
-
Traditional Security Measures vs. Witness AI To Improve Network-Based Observability
See how Witness AI’s network-based observability beats traditional security for enterprise AI.
-
Transform code quality and compliance with automated processes
Learn how GitLab Premium features address the technical debt and security vulnerability challenges that plague traditional approaches.
-
Trending Hybrid Cloud Strategies in 2025 to Tackle Modern IT Infrastructures
Explore top hybrid cloud strategies for 2025, key trends, and why enterprises embrace flexibility, control, and compliance with hybrid models.
-
Trial Opens as Meta Investors Seek Billions Over Privacy Settlement
Meta board members face a rare trial as shareholders seek $8 billion in damages tied to Facebook’s 2019 privacy settlement with the FTC.
-
Troubleshooting Kubernetes with AI: Using the K8s MCP server
Unlock AI-powered Kubernetes troubleshooting! Discover the Model Context Protocol (MCP) and how it standardizes AI agent interactions with Kubernetes tools like kubectl, Helm, and ArgoCD. Learn how to integrate K8s MCP Server with agentic frameworks like PydanticAI for seamless, context-rich cluster management.
-
Turning Migration Into a Strategic Advantage
For fintechs, trust depends on uptime — every transaction must work flawlessly. This article explores how financial technology companies can migrate to AWS without downtime, protecting both performance and reputation. Discover resilience-first strategies like automation, blue/green deployments, and compliance-by-design that turn cloud migration into a strategic advantage rather than a risk.
-
Understand CloudBolt's Orchestration-First Approach To Remove 'Report Factory' In FinOps
Read about CloudBolt’s take on removing ‘report factory’ in FinOps using an orchestration-first approach.
-
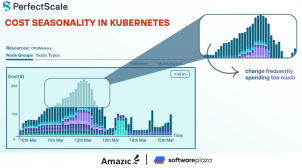
Understanding Cost Seasonality in Kubernetes
Unpack the concept of cost seasonality in Kubernetes, explore the factors that drive its fluctuations, and discover effective strategies—including right-sizing, autoscaling optimization, and leveraging tools like PerfectScale—to manage and predict your cloud spend while maintaining performance.
-
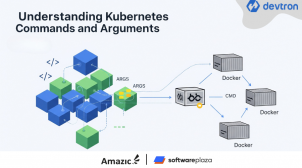
Understanding Kubernetes Commands and Arguments
Want to customize what runs inside your Kubernetes containers? This blog shows you how to use commands and arguments to override Docker defaults, with practical examples and use cases like running startup scripts and testing network connectivity.
-
Understanding SBOM Software: The Foundation of Modern Cybersecurity
A Software Bill of Materials (SBOM) is the key to understanding what’s inside your software—and securing it. This article explores the growing importance of SBOMs in cybersecurity, the difference between static and dynamic SBOMs, how AI is transforming their effectiveness, and best practices for managing software supply chain risk.
-
Unifying the Cloud with HashiCorp: Developer Favorites, HCP Insights & KubeCon Highlights
Melissa Gurney of HashiCorp shares her DevRel journey, explores HCP’s impact, and highlights why developers rely on Terraform, Vault, and Consul—live from KubeCon.
-
Unlimited access to Docker Hardened Images: Because security should be affordable, always
The cost of security shouldn't limit protection. Docker now offers unlimited access to its Hardened Images (DHI) catalog via an affordable subscription. Get near-zero CVEs, a 95% smaller attack surface, and SRLabs-validated security with SBOM/VEX support for every team, from ML workloads to FedRAMP-ready environments.