Login to your Account
Create Affiliate Account
Trouble Signing In?
Enter your email below to request a Reset Password Link
-
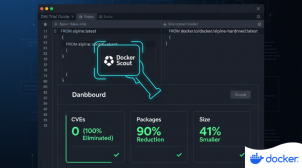
Making the Most of Your Docker Hardened Images Trial – Part 1
Start your DHI trial strong! This guide shows how Docker Hardened Images move you to near-zero CVEs in 3 steps. We compared official Node.js to DHI and found a 100% vulnerability elimination (25 CVEs to 0), a 90% package reduction, and 41% smaller images, validating the compliance benefits with Docker Scout and SBOMs.
-
Turning Migration Into a Strategic Advantage
For fintechs, trust depends on uptime — every transaction must work flawlessly. This article explores how financial technology companies can migrate to AWS without downtime, protecting both performance and reputation. Discover resilience-first strategies like automation, blue/green deployments, and compliance-by-design that turn cloud migration into a strategic advantage rather than a risk.
-
Five Cloud Mistakes Holding Your Fintech Back
Is your cloud bill a sneak attack? Discover the 5 Cloud Mistakes—from ignoring security compliance (POPIA/FSCA) to letting multi-cloud turn into a "digital spiderweb"—that are crippling South African fintechs. Learn the Kinetic Skunk tips for fixing legacy debt and achieving predictable growth.
-
Cloud Is Not a Place… It Is a Strategy
Moving to the cloud isn’t enough. Discover why viewing AWS as a strategy, not a destination, is crucial for fintechs. Learn how to ditch "lift-and-shift," embrace modernization (ECS, Fargate, Lambda), and use Hybrid Cloud to achieve cost predictability and embed compliance like POPIA and FSCA from day one.
-
How Fintechs Can Build Trust Into the Cloud
Discover how fintechs can embed compliance into cloud migrations to enhance security, streamline audits, meet regulations, and build lasting customer trust while enabling scalable innovation.
-
How to Mitigate Risks in Global Supply Chains
The worldwide supply chain is a complex web of interconnected networks, supported by a range of global supply chain services that keep goods flowing across bord
-
AI Threat Detection Tool for Modern Cyber Threats
Discover how AI threat detection transforms cybersecurity by identifying emerging threats, securing AI/ML workloads, and enabling proactive, real-time defense for cloud-native and hybrid environments.
-
AI in Data Security: Risks, Best Practices & Use Cases for Enterprises
Learn how AI in data security is transforming enterprise protection, addressing risks, and enabling compliance. Explore use cases, best practices, and tools like AccuKnox for safeguarding AI workloads.
-
3 ways Sweet Security reduces cloud MTTR by 90%
Read about the main reasons why Sweet Security is the right chose to reduce MTTR and secure cloud workloads.
-
10 Practical Approaches for Cost Optimization in Hybrid Cloud Environments
Cut hybrid cloud costs with 10 proven strategies for visibility, scaling, and smarter compute—all without sacrificing performance or agility.
-
What You Need to Know About Policy as Code in the Era of AI
How PaC evolved from DevOps to AI governance, regulatory compliance, and secure autonomous systems.
-
The state of observability in 2025: a deep dive on our third annual Observability Survey
Dive into Grafana Labs' third annual Observability Survey for 2025! Uncover how observability practices are maturing, why traces are gaining traction, the enduring power of open source, the emerging role of AI, and how cost continues to drive tool selection across organizations of all sizes.