SoftwarePlaza IT Magazine
Login to your Account
Create Affiliate Account
Trouble Signing In?
Enter your email below to request a Reset Password Link
-
Secure Blink on Fixing What’s Broken in Application & API Security
Explore how AI transforms application and API security as Secure Blink co-founder Sonal Khanna discusses THREATSPY, developer-first security, reachability prioritization, recognition, and future-ready API teams.
-
From DevOps to Platforms: How Krumware thinks about real Platform Engineering
Colin Griffin of Krumware discusses platform engineering beyond DevOps, treating platforms as products, culture and UX, pitfalls, and lessons with the CNCF Platforms White Paper.
-
9 Facts You Need to Know About SpiceDB’s Relationship-Based Access Control
Discover how SpiceDB uses ReBAC, low-latency architecture, and centralized authorization to deliver scalable, flexible, and AI-ready access control for modern apps.
-
4 insights into AI, compliance, and modern infrastructure in financial services
Insights into AI adoption, compliance challenges, and modern infrastructure trends shaping financial services, with lessons from real-world transformation.
-
How Beagle Security Helps Organizations Move Beyond Vulnerability Scanners
Discover why traditional scanners fall short and how Beagle Security enables continuous, API-focused testing for faster, stronger application security.
-
10 Things You Need to Know About install4j, The Powerful Multi-Platform Java Installer Builder
Discover why install4j is one of the most reliable multi-platform Java installer builders: features, real-world benefits, and what to know before choosing it.
-
7 Ways AI is Transforming Threat Detection and Cyber Defense
Explore 7 ways AI is reshaping threat detection and cyber defense, from predictive intelligence to adaptive protection for modern security teams.
-
Inside Modern Infra: Kerim Satirli on Terraform, Vault Radar & AI-Safe Workflows
Kerim Satirli returns to unpack HashiCorp’s latest: Terraform Stacks, Actions, Search, Infragraph, and Vault Radar, plus AI-agent rise and supply-chain threats like Shi Hulud attack.
-
Shaping the Future of Documentation: Taylor Dolezal on OSS, Knowledge & Dosu.dev
Taylor Dolezal of Dosu.dev explores living documentation, open-source roots, AI-driven, context-aware knowledge, and Dosu’s fact-and-citation approach to unify fragmented tools for maintainers and enterprises alike.
-
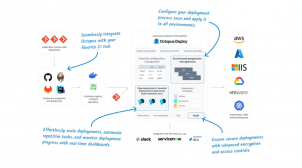
How Octopus Helps Implement Security and Operational Policies for Healthier Platform Adoption
Discover how Octopus Deploy automates security and operational policies to drive healthier, compliant, and developer-friendly platform adoption.
-
How GitKraken MCP Uses AI to Supercharge Your Dev Workflow
GitKraken MCP uses AI and real project context to cut friction, reduce tool switching and turn your coding assistant into a true development teammate.
-
How Formae is Transforming Platform Engineering by Replacing Brittle YAML/JSON
Formae transforms platform engineering with codification, replacing brittle YAML and JSON to create safer, faster infrastructure workflows.