Login to your Account
Create Affiliate Account
Trouble Signing In?
Enter your email below to request a Reset Password Link
-
Lightweight Edge Kubernetes for IoT in Retail & Manufacturing
From factories to remote sites, running Kubernetes at the edge with k3s and MicroK8s under real IoT constraints.
-
How to Achieve Real-Time Visibility with Upwind’s eBPF-Powered Platform
Achieve real-time cloud security with Upwind’s eBPF-powered platform. Learn how runtime visibility reduces noise, stops exploits, and protects AI and Kubernetes workloads.
-
9 Facts You Need to Know About SpiceDB’s Relationship-Based Access Control
Discover how SpiceDB uses ReBAC, low-latency architecture, and centralized authorization to deliver scalable, flexible, and AI-ready access control for modern apps.
-
4 insights into AI, compliance, and modern infrastructure in financial services
Insights into AI adoption, compliance challenges, and modern infrastructure trends shaping financial services, with lessons from real-world transformation.
-
How Beagle Security Helps Organizations Move Beyond Vulnerability Scanners
Discover why traditional scanners fall short and how Beagle Security enables continuous, API-focused testing for faster, stronger application security.
-
10 Things You Need to Know About install4j, The Powerful Multi-Platform Java Installer Builder
Discover why install4j is one of the most reliable multi-platform Java installer builders: features, real-world benefits, and what to know before choosing it.
-
7 Ways AI is Transforming Threat Detection and Cyber Defense
Explore 7 ways AI is reshaping threat detection and cyber defense, from predictive intelligence to adaptive protection for modern security teams.
-
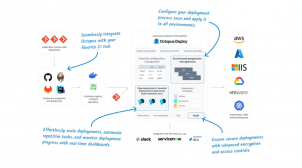
How Octopus Helps Implement Security and Operational Policies for Healthier Platform Adoption
Discover how Octopus Deploy automates security and operational policies to drive healthier, compliant, and developer-friendly platform adoption.
-
How GitKraken MCP Uses AI to Supercharge Your Dev Workflow
GitKraken MCP uses AI and real project context to cut friction, reduce tool switching and turn your coding assistant into a true development teammate.
-
How Formae is Transforming Platform Engineering by Replacing Brittle YAML/JSON
Formae transforms platform engineering with codification, replacing brittle YAML and JSON to create safer, faster infrastructure workflows.
-
7 Ways PointFive Automates Daily Cloud Operations for Efficiency and Scale
Explore seven ways PointFive automates daily cloud operations to cut waste, improve reliability, and scale faster.
-
Check Point Unveils ThreatCloud NextGen: AI-Powered Threat Intelligence for Real-Time Attack Prevention
Check Point unveils ThreatCloud NextGen, an AI-powered threat intelligence platform delivering real-time cyberattack prediction and prevention for modern enterprises.