Login to your Account
Create Affiliate Account
Trouble Signing In?
Enter your email below to request a Reset Password Link
-
AI Networking and Cluster Performance Uplifted by Arista’s Innovations
Learn how Arista is redefining networks to ensure uncompromised AI performance and troubleshooting.
-
AI revolution in DevOps: How Kubiya’s ‘Kubernetes Captain’ transforms operations
Discover how Kubiya.ai's Kubernetes Captain revolutionizes DevOps with AI-driven automation.
-
AI Revolutionizes Banking: How AI Is Already Changing Your Financial World and What’s Next
AI is the hot topic in today’s world, changing how we do business in so many different industries. But perhaps the novelty and remarkable accuracy of AI bots like ChatGPT has obscured just how much AI is already a huge part of our lives, and already a huge part of many industries we already take for granted.
-
AI Threat Detection Tool for Modern Cyber Threats
Discover how AI threat detection transforms cybersecurity by identifying emerging threats, securing AI/ML workloads, and enabling proactive, real-time defense for cloud-native and hybrid environments.
-
Airius Builds Trust With Checkmarx’ MSSP Program
Checkmarx’ AppSec solution helped Airius reduce transacting time, friction, and unnecessary overhead.
-
ALFAGOMMA provides seamless on-demand labeling for customers with enhanced asset management workflows
Learn how integrating BarTender Cloud into AlfaTraka allows customers to track asset usage, maintenance, scheduling, and related notes all from scanning a label.
-
Alibaba to invest $50 billion in AI and cloud computing
Alibaba invests $50B in AI & cloud, aiming for tech breakthroughs. Despite a stock dip, long-term growth & gov backing may solidify its global tech position.
-
Allianz Life Data Breach Hits 1.1 Million Customers
Allianz Life suffers a major cyberattack affecting 1.1 million customers, raising alarms over data security in the insurance sector and driving calls for stronger protections.
-
Alset AI Ventures acquires majority stake in Cedarcross Technologies
Alset AI Ventures acquires a 75% stake in Cedarcross Technologies, strengthening its AI cloud infrastructure leadership.
-
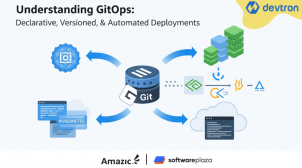
An Introduction to GitOps
This blog introduces GitOps for managing applications and infrastructure using Git, explaining its core principles & benefits like enhanced security, collaboration & automation. It also compares GitOps to CI/CD and highlights how it complements existing DevOps practices.
-
Ana is the World’s First Autonomous AI/ML Engineer
OpenAna launches Ana, an autonomous AI/ML engineer that designs, deploys, and evolves machine learning systems with minimal human input.
-
Anaconda + OpenEye Scientific
OpenEye Scientific, a leader in computational molecular design, has integrated its advanced tools into Orion®, the only cloud-native molecular design platform. To ensure seamless operation and access to vital scientific libraries, OpenEye partnered with Anaconda. Managing Python environments and complex dependencies has historically challenged the scientific community. OpenEye chose Anaconda for its reliability and established leadership in Python package management, enabling straightforward access to numerous scientific libraries that would otherwise be difficult to utilize. Anaconda's embedded solution allows scientific developers to leverage the entire Python ecosystem within Orion, facilitating novel scientific calculations on the cloud. This partnership creates a seamless, powerful experience for Orion users, making advanced molecular design more accessible than ever.