Login to your Account
Create Affiliate Account
Trouble Signing In?
Enter your email below to request a Reset Password Link
-
Red Hat OpenShift AI Flaw Puts Hybrid Cloud Systems at Risk of Full Takeover
A critical flaw in Red Hat OpenShift AI (CVE-2025-10725) lets low-privileged users gain full cluster control, putting hybrid cloud AI workloads at serious risk.
-
Hackers Claim Theft of Nearly 1 Billion Salesforce Records, But Company Denies Breach
Hackers claim to have stolen 1 billion Salesforce records, but the company claims there was no breach, just social engineering of customers.
-
Unlimited access to Docker Hardened Images: Because security should be affordable, always
The cost of security shouldn't limit protection. Docker now offers unlimited access to its Hardened Images (DHI) catalog via an affordable subscription. Get near-zero CVEs, a 95% smaller attack surface, and SRLabs-validated security with SBOM/VEX support for every team, from ML workloads to FedRAMP-ready environments.
-
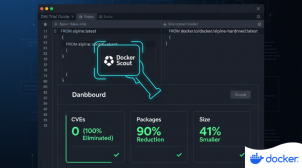
Making the Most of Your Docker Hardened Images Trial – Part 1
Start your DHI trial strong! This guide shows how Docker Hardened Images move you to near-zero CVEs in 3 steps. We compared official Node.js to DHI and found a 100% vulnerability elimination (25 CVEs to 0), a 90% package reduction, and 41% smaller images, validating the compliance benefits with Docker Scout and SBOMs.
-
Atlassian Buys Developer Productivity Startup DX in $1 Billion Deal
Atlassian makes its biggest acquisition yet, buying developer productivity platform DX for $1B to strengthen its software suite.
-
Docker Hardened Images: crafted by humans, protected by AI
Docker’s Hardened Images (DHI) are secured by a dual approach: human expertise backed by AI. Discover how Docker’s internal AI guardrail spotted a critical logic flaw in an nginx-exporter update, blocked the release, and contributed the fix upstream, proving AI is the best force multiplier for security architects
-
Expanding Docker Hardened Images: Secure Helm Charts for Deployments
Docker is simplifying Kubernetes security! Discover how new Helm charts in the Docker Hardened Images (DHI) Catalog give users a secure, compliance-ready alternative after the Broadcom/Bitnami changes. Deploy DHI by default, ensuring SLSA Level 3 security and SLA-backed patching for every Kubernetes workload.
-
From Infrastructure-as-Code to Policy-as-Code: Automating Governance in Multi-Cloud Environments
Understand the evolution of IaC to PaC and how leading players such as HashiCorp and Pulumi are helping companies
-
4 Investments To Make In Cloud Security In 2026
Read everything about the current challenges in protecting assets and new trends in cloud security in 202
-
Apple Faces Lawsuit From Authors Over AI Book Training
Apple faces a lawsuit from authors alleging it used copyrighted books to train AI without consent, sparking wider questions about creativity and compensation.
-
7 Hidden Complexities of Cloud Data Management That CloudQuery Can Resolve
Discover seven hidden complexities of cloud data management, including privacy, API limits, scale, vendor lock-in, latency, transformations, and AI compliance, and learn how CloudQuery simplifies them with secure, flexible, and AI-ready solutions.
-
How to Overcome Challenges While Running Serverless at Scale with WebAssembly
Discover how WebAssembly overcomes the challenges of running serverless at scale. Learn about faster startups, lower costs, Kubernetes integration, and edge computing with WebAssembly.