Cybersecurity has taken center stage in the world of on-premise systems to sprawling multi-cloud environments. From traditional malware to AI-driven threats, the evolving digital ecosystem is both a marvel and a minefield.
This blog post focuses on how DOT security helps organizations understand the complex world of cloud security and the various uses of AI in cybersecurity.
Navigating a world of cloud complexity
The cloud has enabled organizations to scale quickly and adopt modern DevOps practices, but with that agility comes complexity. Businesses often juggle legacy tech, hybrid infrastructure, SaaS sprawl, and multi-cloud deployments while trying to maintain security visibility and control.
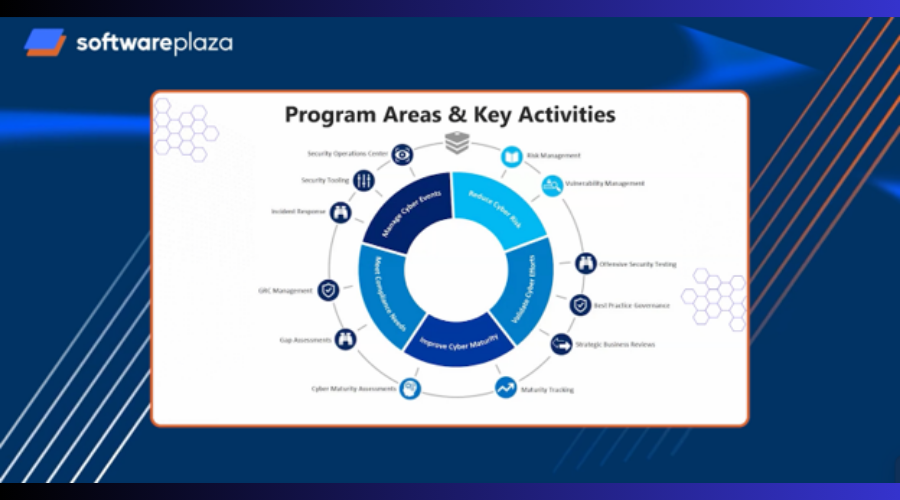
DOT Security helps organizations cut through this complexity by applying a broad-based, technology-agnostic security strategy. Instead of focusing on a single niche, DOT provides end-to-end services that address the five key pillars of cloud security:
- Reducing cyber risk
- Validating cybersecurity controls
- Improving cyber maturity
- Meeting compliance requirements
- Managing real-time incidents
Shift left, but with security in mind
One of the most important phenomena in recent times is the “shift left” movement. Today, development teams are empowered to provide infrastructure and deploy code faster than ever. But with great power comes great responsibility. Many developers now manage environments they weren’t traditionally trained for, which can lead to security gaps.
Businesses must have dedicated resources within developers' teams who understand where and how to deploy secure environments. Without cybersecurity awareness built into the development pipeline, businesses risk constructing fragile foundations that can be easily exploited.
The burden of technical debt and resource strain
Many organizations are still weighed down by technical debt, outdated systems that are still integral to operations but prone to vulnerabilities. DOT Security often works with companies that know they need better digital hygiene but don’t know where to start.
Resource limitations compound these challenges. The key to solving this isn’t just more tools, but smarter alignment of people, process, and technology. DOT’s approach involves understanding clients’ unique threat profiles, performing vulnerability assessments, and building a comprehensive risk register.
The double-edged sword of AI in cybersecurity
Artificial Intelligence is central to a new wave of security innovation and threats. Jeff described AI adoption in three key areas:
- Productivity Enhancement: Developers and professionals use generative AI (like GitHub Copilot or ChatGPT) to write code, brainstorm solutions, and automate documentation.
- Security Strategy: DOT helps clients understand the risks of AI integration, draft AI policies, and ensure proper data governance for AI systems.
- Attack Vector: Threat actors are using AI, too. DOT has observed “dark AI” applications that can assist attackers with generating malware, automating reconnaissance, and launching exploits, including prompt injection and hallucinated package vulnerabilities that trick developers into installing malicious code.
How DOT Security uses AI for defense
DOT Security is incorporating AI and machine learning into its technology stack to stay ahead. Their blue team leverages AI-powered threat detection and response systems, which ingest billions of logs and events to surface real-time risks.
Their red team uses autonomous penetration testing tools alongside certified human experts to uncover deep vulnerabilities far beyond traditional scanning. The V-CISO service helps clients understand their evolving risk posture, especially as AI-enabled attacks grow more sophisticated.
Since it is impossible to defend against AI-enabled attackers with yesterday’s tools, businesses need to adopt and evolve their systems simultaneously.
Consolidated tools with open architecture
Tool sprawl is another common pain point in cybersecurity. DOT’s approach to tooling is balanced, and they prefer consolidated platforms that offer integrated capabilities but avoid vendor lock-in. This rigorous approach involves real-world testing, simulated attacks, and support quality, pricing, and extensibility assessments.
DOT leans into platforms that provide:
- Autonomous security testing
- AI/ML-powered threat detection
- API extensibility for integration
- Scalability for future evolution
This open-yet-opinionated approach ensures that clients benefit from best-in-class tech while retaining flexibility.
From consulting to continuous coverage
DOT Security’s services span the entire security lifecycle. Here’s a breakdown of their offerings:
- Risk and Compliance Consulting: Virtual CISO (vCISO) services and cyber maturity assessments help align security with business goals.
- Red Team / Offensive Security: Continuous and project-based penetration testing to uncover critical vulnerabilities.
- Blue Team / SOC Operations: AI-powered monitoring, detection, and incident response to protect environments in real time.
- Compliance Assurance: Support for frameworks like CMMC, NIST, and others, especially for defense contractors and manufacturers.
DOT's unified approach ensures clients aren’t just checking boxes, but building real cyber resilience.
Cloud-native and AI-native futures
The conversation wrapped up with a look ahead. With Google’s acquisition of Wiz, and Microsoft expanding its CNAPP (Cloud-Native Application Protection Platform) offerings, Jeff sees the industry moving toward consolidated, AI-native platforms.
But even the best tools need context. There is still a need for humans who understand and can act on the data. DOT’s mission is to bridge that gap, helping organizations adopt cutting-edge tech without losing sight of strategy and execution.
Final thoughts
Cloud security is dynamic and challenging, but also full of opportunity. AI, DevOps, and hybrid cloud architectures are changing how businesses operate and how they’re attacked. DOT Security stands at this intersection, providing organizations with the tools, strategies, and services they need to stay secure in an unpredictable world.
From proactive assessments to AI-driven detection and real-time incident response, DOT is helping businesses not just react to threats but also get ahead of them.
To learn more, visit DOT Security and explore how they can help you confidently secure your cloud environments and AI initiatives.
This blog is based on a recent episode of the Software Plaza podcast, Jeff Leader, CTO at DOT Security, shared deep insights into how his team is redefining cloud security and why artificial intelligence (AI) is both a threat and a tool in this evolving equation.
Featured Image Source: Webinar
Understand the the impact of AI on cloud security and how DOT Security is making waves