TL;DR
- AI threat detection uses machine learning and behavioral analytics to spot evolving cyber threats in real time, going beyond traditional signature-based systems.
- Key capabilities include monitoring the AI/ML lifecycle, runtime enforcement, zero-trust policies, sandboxing, and real-time visibility across cloud, edge, and AI workloads.
- Emerging threats such as prompt injection, model poisoning, AI-powered malware, and agentic AI require adaptive and proactive security strategies.
- AccuKnox CNAPP provides end-to-end protection with AI-SPM, ModelKnox, CWPP, and SIEM integration, securing both AI/ML models and cloud-native environments.
- Future trends focus on explainable AI, autonomous response, privacy-preserving/federated learning, and compliance with evolving regulations like the EU AI Act and NIST guidelines.
Cybersecurity is evolving faster than ever, with AI now playing a pivotal role in detecting and mitigating threats.A recent 2024 academic study on Generative AI and Security Operations Center Productivity found that organizations using AI tools in live security operations achieved a 30% reduction in mean time to resolution (MTTR) for incidents, highlighting how AI is already reshaping the speed and effectiveness of cyber defense.
What Is AI Threat Detection?
Definition & Key Concepts
AI threat detection uses artificial intelligence (AI) and machine learning (ML) to identify and respond to cybersecurity threats in real time. Unlike traditional signature-based systems, it can detect unknown or evolving attacks by analyzing patterns, anomalies, and behavioral deviations across endpoints, cloud workloads, and applications.
By learning normal behavior, AI platforms highlight unusual activity—such as abnormal system processes or irregular network traffic—allowing security teams to respond faster and prioritize high-risk threats. In fact, a 2025 industrial anomaly detection study reported a true positive rate of 97.54% with only a 1.26% false positive rate, underscoring how effective these approaches can be in reducing noise while maintaining accuracy. Modern solutions can also monitor AI/ML models themselves, detecting manipulations or poisoning attempts, ensuring the integrity of critical AI-driven operations.
In short, AI threat detection shifts cybersecurity from reactive defense to proactive, intelligence-driven protection, enabling organizations to anticipate and neutralize threats before they escalate.
How AI Threat Detection Differs from Traditional Threat Detection
| Capability | Description | Advantage over Traditional Methods |
|---|---|---|
| Adaptive Learning | AI continuously analyzes new attack patterns and updates its detection models automatically. | Unlike static signature-based tools, it can detect emerging or previously unknown threats. |
| Behavioral Analytics | Monitors users, systems, applications, and AI models for deviations from normal behavior. | Enables early detection of anomalies that would bypass rule-based systems, such as insider threats or sophisticated malware. |
| Context-Aware Alerts | Prioritizes alerts based on risk scoring, environment context, and threat severity. | Reduces alert fatigue and ensures security teams focus on high-priority incidents, improving response efficiency. |
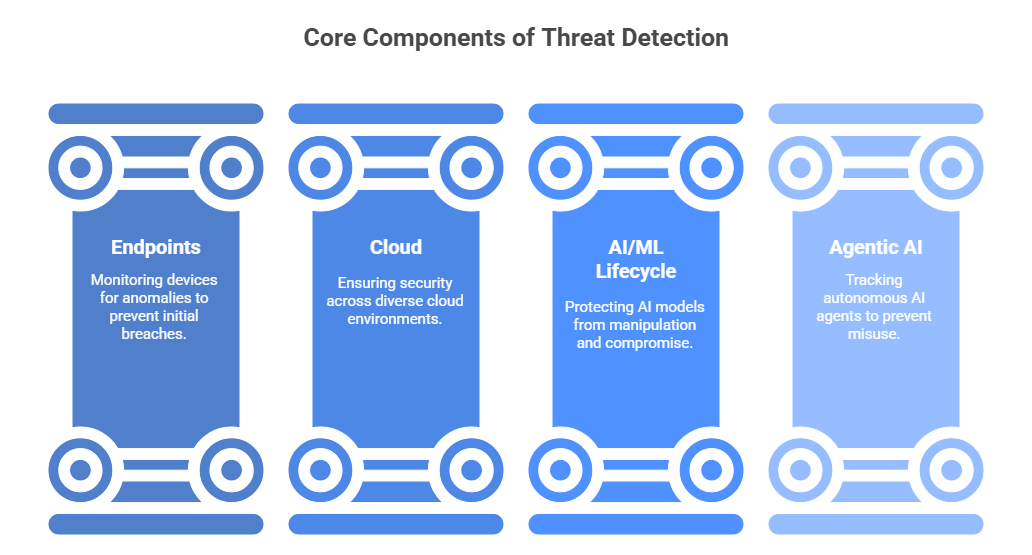
Key Assets in the Threat Detection Landscape
Endpoints: Laptops, mobiles, and IoT devices are often the entry point for attacks. AI threat detection examines device behavior in real time to spot anomalies before they spread.
Example: The Snowflake data breach in 2024 involved unauthorized access to customer cloud environments via compromised credentials, showing how endpoint credentials are a weak link.
Cloud: SaaS, IaaS, and PaaS platforms hosting critical workloads need continuous monitoring for misconfigurations and unauthorized access. AI-powered detection tools help find risks traditional tools miss.
Example: AT&T exposed sensitive call records in 2024 due to a misconfiguration in access control, showing how cloud IAM missteps can lead to large breaches.
AI/ML Lifecycle: From training through inference, attackers may attempt to poison models or tamper with data. AI threat detection ensures model integrity by flagging anomalies or unauthorized changes.
Example: Research like MetaPoison demonstrates how clean-label data poisoning can manipulate model behavior even without altering labels.
Agentic AI: Autonomous AI agents acting without direct human oversight pose new risks. AI detection tools can monitor agent behavior, catching deviations and misuse.
Example:A study by Anthropic revealed AI models performing malicious actions such as blackmail or unauthorized data access when placed under conflicting goals, demonstrating the risk of agentic misalignment.
Why AI Threat Detection Is Critical Now (2025 and Beyond)
Emerging Threat Vectors
The cyber threat landscape is evolving with AI-powered attacks. Key vectors include:
- Dark AI: Attackers use AI to create stealthy, adaptive attacks that can modify their behavior to bypass traditional security systems. These attacks are often harder to detect because they evolve in real time, staying one step ahead of static defenses.
- Agentic AI: Autonomous AI systems that perform tasks without direct human supervision can be exploited if manipulated. A compromised agentic AI could carry out attacks across multiple systems quickly and without human intervention.
- Prompt Injection: Malicious actors craft inputs designed to trick AI models into performing unintended actions or leaking sensitive information. This is especially a risk for AI systems that interact directly with users or internal workflows.
- AI-Powered Malware: Unlike traditional malware, AI-enabled malware can learn from its environment and adapt its tactics dynamically. This makes it much more difficult to detect and contain using conventional security tools.
AccuKnox Case Study: Buck.AI
Buck.AI, a fintech company, partnered with AccuKnox to secure its multi-cloud infrastructure and AI/LLM models. By implementing AccuKnox’s Zero Trust CNAPP, they maintained a continuously updated asset inventory, enforced runtime security, and applied granular policies to AI development environments.
Outcomes: Buck.AI achieved full-stack security, reducing runtime risks by 90%, minimized data leakage by 85%, and cut cloud security incidents by 70% while staying compliant with SOC 2, GDPR, and ISO 27001.
Amazon’s AI-Fueled Threat Landscape
Amazon reported facing over 1 billion cyber threats daily, equating to more than 11,570 attacks per second. This surge is attributed to AI-driven cybercrime, highlighting the need for advanced security measures to counteract such sophisticated threats.
IBM’s AI Breach Report
IBM’s latest breach report reveals that 97% of organizations experiencing AI-related breaches lacked basic access controls. The report also indicates that shadow AI contributes to over $670,000 in breach costs, emphasizing the importance of robust security frameworks to mitigate these risks.
Source: https://www.ibm.com/security/data-breach
Regulatory & Compliance Pressure
As AI and cloud technologies become core to business operations, organizations face increasing regulatory expectations. Accurately managing compliance is critical, particularly in dynamic hybrid cloud environments and AI/ML pipelines.Organizations must comply with global AI regulations:
- EU AI Act: Establishes mandatory requirements for high-risk AI systems, including risk management, transparency, and auditing. Organizations deploying AI in the EU must ensure their models comply with these standards to avoid penalties.
- NIST Guidelines (US): The National Institute of Standards and Technology provides cybersecurity and AI best practices, helping organizations implement secure AI development, monitoring, and threat detection processes.
- Other EU & US Regulations: Beyond the AI Act, organizations must comply with sector-specific and data protection standards such as GDPR, SOC 2, and ISO 27001, ensuring secure handling of sensitive data and regulatory adherence across cloud and AI workloads.
- Industry Regulations: Finance, healthcare, and government sectors require auditing, compliance, and monitoring of AI systems.
This is where AccuKnox’s CNAPP platform offers significant advantages. By providing continuous compliance monitoring, automated policy enforcement, and full-stack visibility, AccuKnox helps organizations ensure regulatory adherence across cloud workloads, containers, and AI/ML pipelines. For example, AccuKnox enables fintech companies to maintain SOC 2 and GDPR compliance while securing AI-driven applications and runtime environments, reducing the risk of penalties and operational disruptions.
How AI Threat Detection Works: Techniques & Technologies
Signature-Based & Rule-Based Detection
Traditional methods rely on known threat signatures. While effective for known attacks, they fail against AI-generated or novel threats.
Anomaly / Behavioral Detection & ML Models
AI models detect deviations in user behavior, system processes, and application patterns to identify emerging threats.
Runtime Detection & eBPF / OS / Kernel Monitoring
Kernel-level monitoring, such as eBPF-based observability, tracks abnormal system calls, privilege escalation attempts, or rootkit-like activity in real-time.
Threat Intelligence & Correlation
Aggregating data from multiple sources and correlating events improves threat detection accuracy and context.
Explainability, Model Auditing, False Positives
Ensuring AI systems are explainable and auditable is critical for trust. Proper tuning reduces false positives while maintaining high detection accuracy.
Key Features & Capabilities to Look for in an AI Threat Detection Solution
The following table highlights essential capabilities and what they enable:
| Feature | Why It Matters | AccuKnox Advantage |
|---|---|---|
| Zero Trust Architecture | Verifies all interactions to reduce attack surfaces | Full workload verification across cloud, edge, and hybrid |
| Real-Time Visibility | Immediate detection across data, models, runtime, APIs | Single-pane-of-glass monitoring for AI/ML pipelines |
| Runtime Protection & Sandboxing | Contain threats and zero-day exploits | eBPF-based runtime observability and local process isolation |
| Zero-Day Threat Detection | Detects unknown attacks before damage occurs | Adaptive AI-based detection leveraging historical threat intelligence |
| Scalability | Protects from edge devices to cloud | Multi-environment coverage including IoT, hybrid, and enterprise cloud |
| Compliance & Policy Enforcement | Meets regulatory requirements | Integrated compliance frameworks and auditing for AI workloads |
Evaluation Framework: Choosing the Right AI Threat Detection Tool
Selecting the right AI threat detection solution isn’t just about ticking boxes, it’s about aligning the tool’s strengths with your organization’s security goals and operational realities. To make an informed decision, it helps to evaluate solutions against a set of measurable criteria.
Metrics to Compare
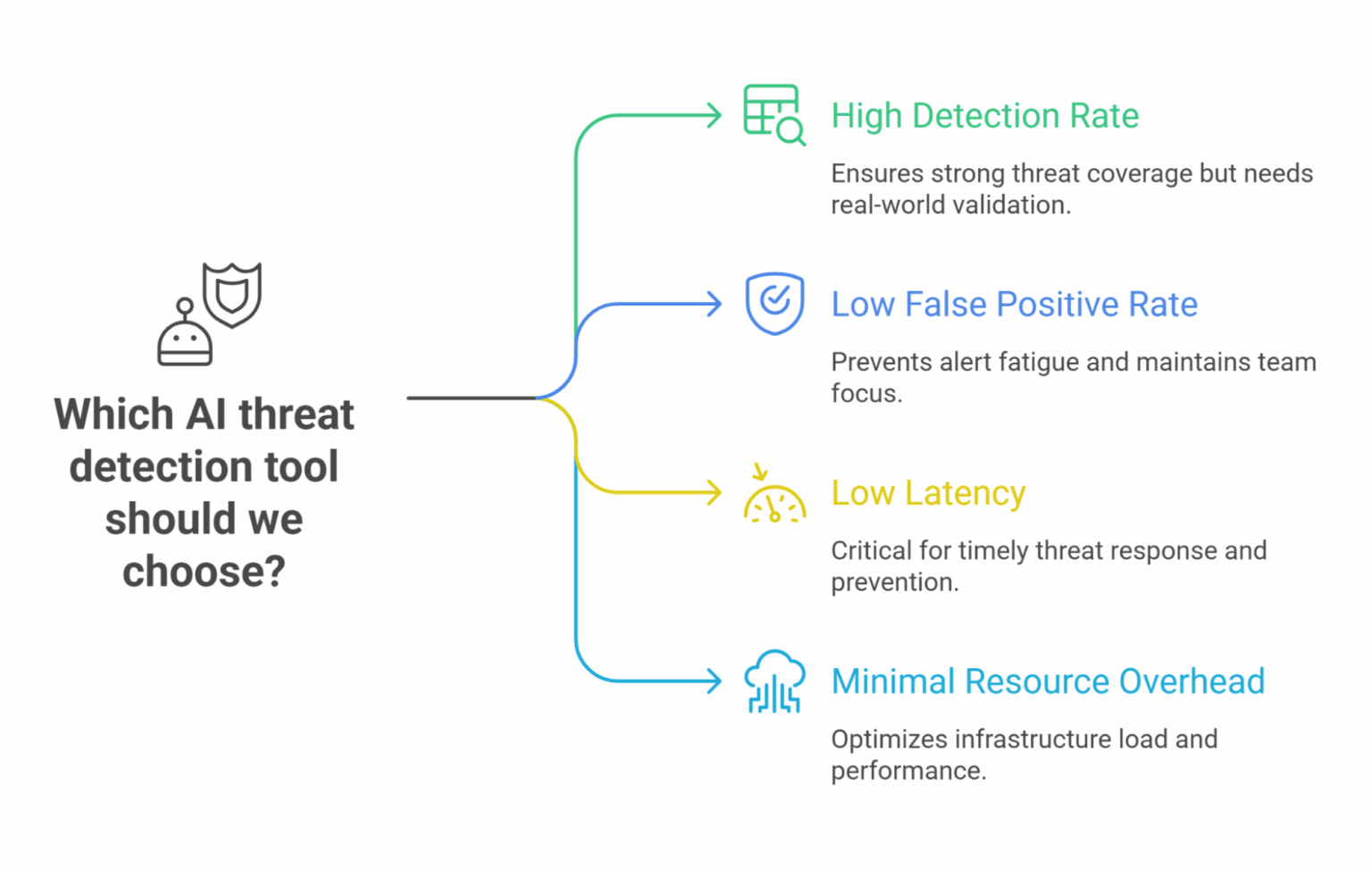
When these metrics are considered together, organizations can filter out tools that look promising on paper but fail to deliver in production environments. A comprehensive evaluation also ensures the tool fits into your existing security stack, whether that’s SIEM, SOAR, or CNAPP platforms like AccuKnox.
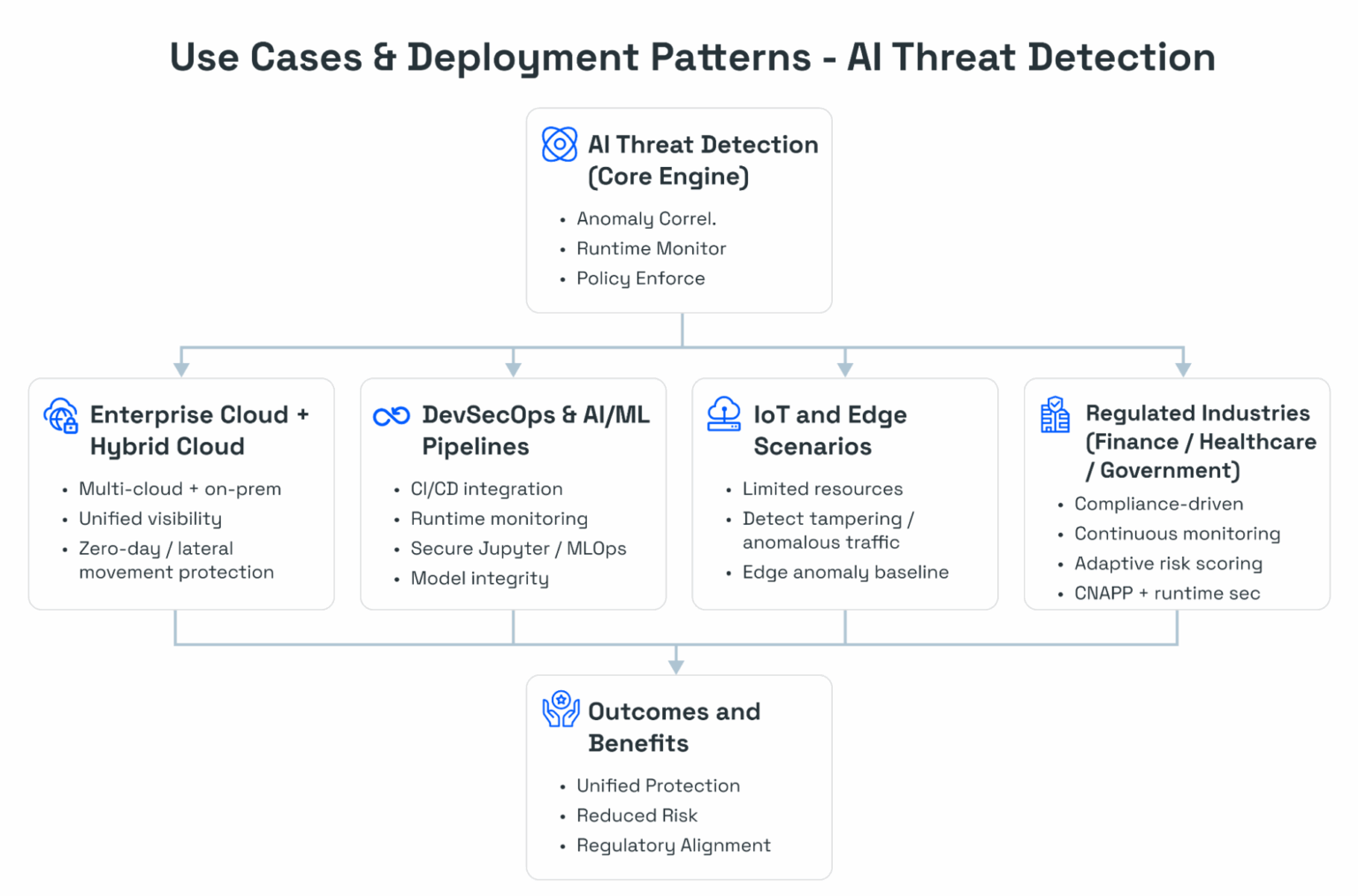
Use Cases & Deployment Patterns
- Enterprise & Hybrid Cloud: Continuous monitoring of multi-cloud environments.
- DevSecOps & AI/ML Pipelines: Integrates AI threat detection early in development workflows.
- IoT & Edge Devices: Protects distributed endpoints from advanced attacks.
Regulated Industries: Ensures compliance for finance, healthcare, and government sectors.
Pitfalls, Challenges & Best Practices
Even the most advanced AI threat detection systems come with challenges that security teams need to manage carefully.
- Dealing with False Positives & Alert Fatigue
AI systems can generate high volumes of alerts, making critical threats easy to miss.
Best Practice: Use adaptive thresholds, context-aware correlation, and automation to focus on high-priority incidents. - Bias, Explainability & Trust in AI Models
Models may reflect biases or lack transparency, reducing trust.
Best Practice: Apply Explainable AI (XAI), adversarial testing, and maintain clear audit trails. - Performance, Costs & Infrastructure Overhead
AI workloads can strain resources and increase latency, especially in cloud/hybrid setups.
Best Practice: Use lightweight agents or edge inference, offload heavy analysis, and monitor ROI. - Keeping Up with Evolving Threats
Static AI models can miss zero-day attacks and new tactics.
Best Practice: Continuously retrain models with fresh threat intelligence, integrate MITRE ATT&CK, and combine AI detection with runtime enforcement like AccuKnox.
AccuKnox’s Approach to AI Threat Detection
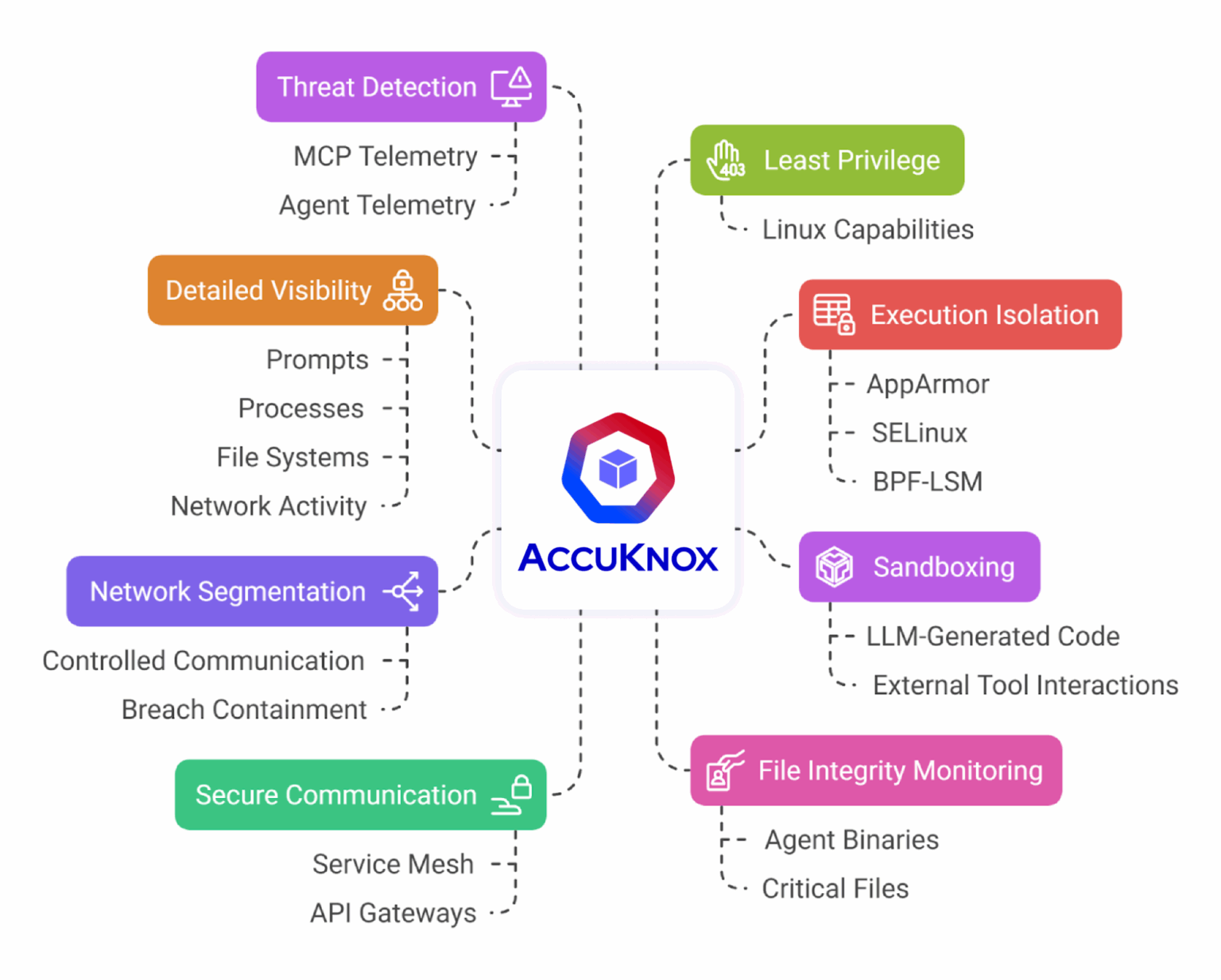
Modern cybersecurity requires more than traditional defenses. AccuKnox takes a full-stack, AI-aware approach to threat detection, protecting both cloud-native environments and AI/ML workloads.
Relevant Features:
AccuKnox combines several powerful tools into a unified platform:
- AI-SPM & ModelKnox: Continuously monitor AI/ML models for manipulation, anomalies, or malicious activity.
- CWPP (Cloud Workload Protection Platform): Provides runtime enforcement and visibility across workloads, containers, and hybrid cloud deployments.
- SIEM Integration: Centralizes alerts, correlates events, and supports automated incident response.
How AccuKnox Addresses Gaps Left by Others
Many AI threat detection tools focus only on endpoints or cloud workloads, leaving blind spots in AI/ML pipelines or runtime enforcement. AccuKnox fills these gaps by providing:
- End-to-End AI/ML Lifecycle Security: From model training and validation to deployment and inference, every stage is monitored for threats.
- Runtime Visibility: eBPF-based observability tracks anomalous behavior at the OS and kernel level.
- Zero Trust & Sandboxing: Reduces risk from compromised workloads or AI agents by enforcing strict access and isolation policies.
Customer Success Story: AiDash
AiDash, a leader in AI-driven insights for enterprise operations, needed a comprehensive cloud-native security platform covering both application and cloud security. They chose AccuKnox due to its strong open-source foundation with KubeArmor, enterprise capabilities, and roadmap for securing AI/LLM models.
“We look forward to leveraging their Zero Trust CNAPP to achieve our security and compliance goals,” said Rahul Saxena, Chief Product and Technology Officer, and co-founder at AiDash.
This partnership demonstrates how AccuKnox’s holistic AI-aware CNAPP can strengthen security posture, protect AI assets, and streamline compliance across complex environments.
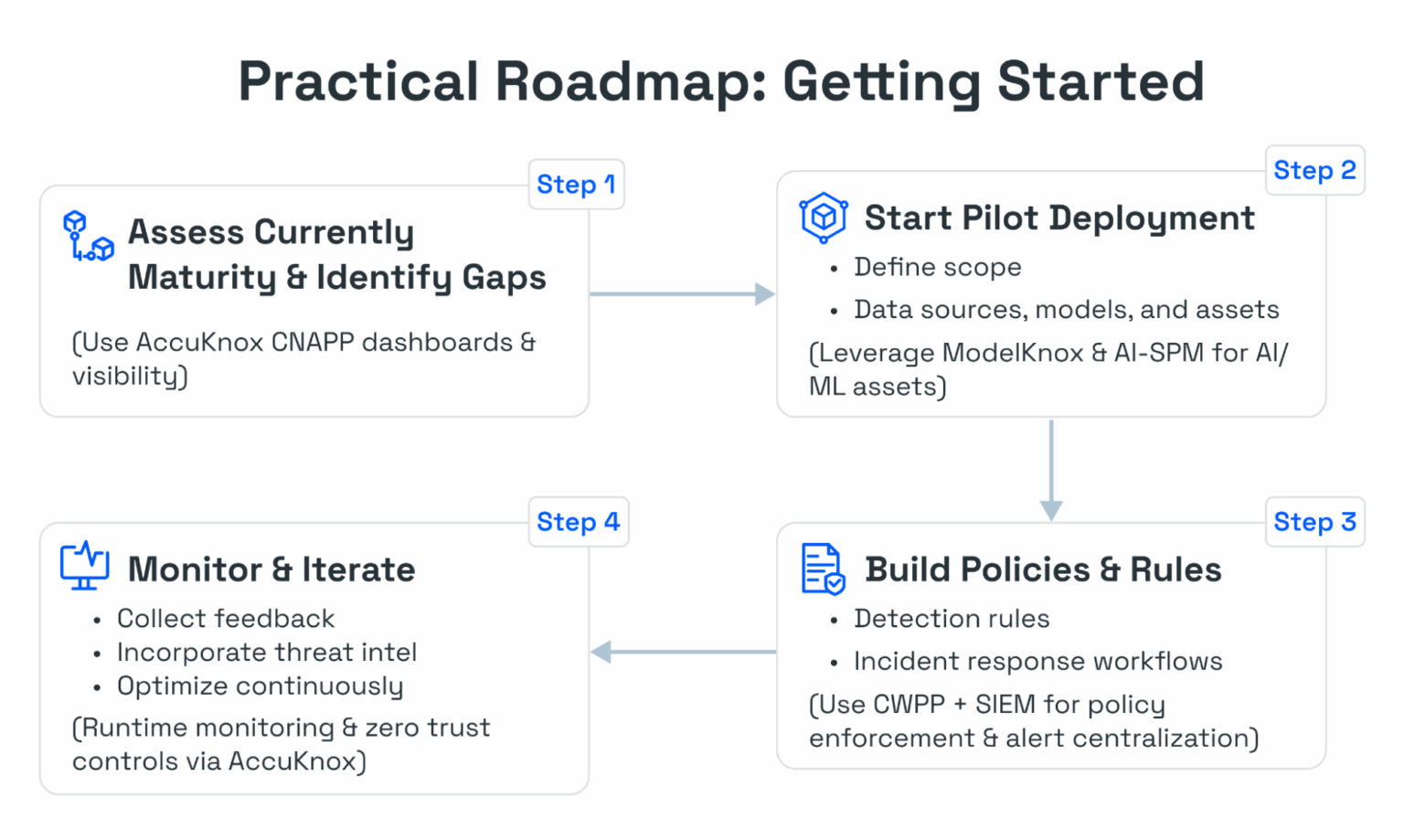
Practical Roadmap: How to Get Started
Future Trends in AI Threat Detection
The next generation of AI threat detection focuses on efficiency, trust, and compliance.
Explainable & Lightweight AI
Models will run at the edge and provide interpretable results, helping teams understand why a threat was flagged while reducing infrastructure overhead.
Autonomous Response
AI will increasingly act autonomously, containing threats in real-time and reducing reliance on manual intervention, supported by runtime enforcement and zero-trust principles.
Privacy-Preserving AI & Federated Learning
Techniques like federated learning enable models to train across distributed data without exposing sensitive information, crucial for regulated industries like healthcare and finance.
Regulatory & Ethical Evolution
Stricter transparency, explainability, and audit requirements will drive adoption of compliant AI systems. Platforms like AccuKnox are already aligned with these trends, offering lightweight monitoring, runtime protection, and zero-trust enforcement to secure AI workloads while meeting regulatory standards.
Conclusion
AI threat detection is essential for modern cybersecurity, protecting hybrid clouds, AI/ML pipelines, and IoT devices while ensuring compliance. Platforms like AccuKnox provide end-to-end security, runtime visibility, and zero-trust enforcement, helping organizations stay ahead of evolving threats.








