TL;DR
- AI enhances data security by automating data classification, monitoring anomalies, enforcing policies, and preventing breaches across cloud-native and hybrid environments.
- Real-time threat detection powered by AI helps identify insider threats, prompt injections, and unusual access patterns, reducing incident response times.
- Best practices like zero trust, privacy-preserving AI, runtime controls, and compliance alignment help secure AI pipelines from training to inference.
- AccuKnox provides AI-focused runtime protection, ModelArmor, and AI Copilot tools for proactive threat detection, policy enforcement, and audit-ready visibility.
- Measuring effectiveness through false positives, encrypted data coverage, MTTD/MTTR, and compliance readiness ensures AI-driven security works reliably.
Why AI in Data Security Is Now Critical
Artificial intelligence (AI) has rapidly transformed how organizations manage data, streamline processes, and gain insights. From automating routine tasks to powering predictive analytics, AI is now embedded in core business operations. However, as its adoption grows, so do the risks associated with data privacy and security in AI. Organizations must not only protect their traditional IT systems but also safeguard training datasets, inference pipelines, and AI model endpoints.
The convergence of AI and cybersecurity priorities means that security teams need to anticipate AI-specific threats and implement real-time defenses. This includes monitoring AI models for unusual behavior, securing sensitive data used in training, and ensuring that policies are enforced across hybrid and cloud-native environments. In this guide, we’ll explore key use cases, challenges, and best practices, along with insights on designing secure AI architectures and measuring effectiveness.
Key Use Cases of AI in Data Security
AI is not only a source of potential risk, it’s also a powerful ally in defending digital environments. Here’s how organizations are leveraging AI to enhance data security:
Data Classification and Access Control
AI can automatically scan large volumes of structured and unstructured data, tagging sensitive content and assigning appropriate access controls. This ensures that critical datasets are only accessible to authorized users, reducing the likelihood of accidental leaks or insider misuse.
Anomaly Detection and Threat Response
By continuously monitoring system behaviors, AI detects abnormal access patterns, unusual data transfers, or deviations from standard workflows. This allows security teams to respond faster to potential breaches and mitigate threats before they escalate.
Data Loss Prevention (DLP) Automation
AI-driven DLP tools can automatically identify sensitive content in motion or at rest, enforcing policies to prevent accidental or malicious data leaks. This reduces reliance on manual interventions and ensures consistent enforcement across complex IT environments.
Insider Threat Detection Using Behavioral Patterns
Not all threats originate outside the organization. AI can monitor employee or workload behaviors to detect anomalies, such as unusual login times, attempts to access restricted files, or unusual data-sharing activity, flagging potential insider risks early.
Adaptive Encryption and Real-Time Policy Enforcement
Dynamic, context-aware encryption can protect sensitive data wherever it resides—whether on-premises, in a hybrid cloud, or across multi-cloud deployments. AI can enforce policies in real time, adjusting protections based on risk, sensitivity, or location of the data.
Challenges of Using AI in Data Security
While AI strengthens security, it introduces its own set of risks:
- Expanded Attack Surface: AI models can be exploited through inference attacks or adversarial inputs, revealing sensitive information or bypassing defenses.
- Data Privacy and Compliance Concerns: Training AI requires large datasets, which often include personal or regulated data. Organizations must ensure privacy while meeting standards like GDPR, HIPAA, or SOC2.
- Adversarial Inputs and Model Poisoning: Malicious actors can inject corrupt data into training pipelines, influencing model outputs or creating vulnerabilities.
- Visibility and Control Gaps: Many organizations lack complete monitoring across AI pipelines, creating blind spots for security incidents.
According to a Pew Research Center survey, 81% of consumers think the information collected by AI companies will be used in ways people are uncomfortable with. Addressing these challenges require a combination of strategies, such as end-to-end observability, runtime protection, and proactive policy enforcement that not only secure AI models but also protect the sensitive data they process.
AI-Powered Data Security Best Practices
The global AI in cybersecurity market was valued at $22.4 billion in 2023 and is projected to reach $60.6 billion by 2028, growing at a CAGR of 21.9%. To secure AI deployments, organizations can adopt several key strategies:
| Best Practice | What It Covers | Examples |
|---|---|---|
| Implement Zero Trust in AI Pipelines | Treats every AI process, data flow, and model interaction as untrusted; validates all access and isolates workloads. | Restricting dataset access, micro-segmentation in Kubernetes, enforcing MFA for model endpoints. |
| Build Privacy-Preserving AI Models | Uses advanced techniques to learn patterns without exposing sensitive data. | Differential privacy in healthcare AI, federated learning for financial institutions, homomorphic encryption in cloud training. |
| Enforce Runtime Controls | Monitors AI behavior at runtime to detect anomalies and block suspicious activity. | AccuKnox ModelArmor for runtime enforcement, anomaly alerts on inference APIs, blocking unauthorized queries. |
| Ensure Auditability and Explainability | Makes AI decisions transparent and traceable with logs and explainable AI (XAI). | Model audit trails for HIPAA compliance, SHAP values in ML models, explainable credit scoring systems. |
| Align AI Deployments with Compliance Mandates | Embeds regulatory compliance directly into AI workflows from ingestion to inference. | GDPR-aligned data handling, HIPAA-compliant PHI protection, SOC 2 controls in AI pipelines. |
How AccuKnox Helps Secure AI Workloads
While these practices provide a strong foundation, organizations often need dedicated tools to operationalize them. AccuKnox offers a suite of AI-focused security solutions that help enterprises protect AI workloads and sensitive data across cloud-native and hybrid environments.
Key Features
- ModelArmor: Provides runtime protection for ML/AI models while monitoring behavior to prevent exploitation and unauthorized access.
- AI Copilot: Delivers AI-assisted insights and recommendations to enforce security policies and detect anomalies in real time.
- AI Security Platform: Offers comprehensive observability across workloads, enabling zero-trust enforcement, policy management, and audit-ready logs.
Real-World Benefits
- Proactive Threat Detection: By monitoring AI models and workloads at runtime, AccuKnox helps detect abnormal behavior before it impacts operations.
- Policy Enforcement and Compliance: Ensures sensitive data remains protected, supporting GDPR, HIPAA, and other regulatory standards.
- Seamless Integration: Works across Kubernetes, VMs, and cloud-native infrastructure, fitting naturally into DevSecOps workflows.
This dedicated approach allows enterprises to not only identify and mitigate risks but also operationalize AI security in a scalable manner in real time.

Designing a Secure Architecture for AI in Data Security
A secure AI architecture ensures protection throughout the entire AI lifecycle:
- Secure Data Ingestion: Validate and sanitize data before feeding it into training pipelines.
- Controlled Training and Inference: Enforce access policies and encrypt sensitive datasets.
- Integration into DevSecOps: Monitor AI models continuously, integrate runtime enforcement, and automate policy applications.
- Policy Enforcement: Platforms like AccuKnox provide runtime security, ensuring workloads and AI models operate within predefined risk parameters.
Embedding security early and continuously reduces the chance of vulnerabilities while ensuring AI models remain trustworthy and compliant.
Data Security via AccuKnox AI Security
Organizations are already seeing tangible benefits from AI-driven security:
- Preventing Unauthorized Access: AI detects suspicious activity in cloud workloads, preventing data breaches.
- Mitigating Prompt Injection and Model-Level Threats: Continuous monitoring ensures AI models, including LLMs, remain uncompromised.
- Securing Sensitive Datasets: AI automatically classifies and encrypts data, protecting PHI, PII, and other regulated datasets.
- Automating Compliance Reporting: AI-driven insights streamline audit reporting, reducing manual effort and errors.

Platforms like AccuKnox, provide runtime visibility to enterprises, enabling them to enforce AI-driven security measures in real time, ensuring that they are effective, and aligned with regulatory requirements.
Metrics to Measure the Effectiveness of AI in Data Security
Quantifying security performance is critical:
- Reduction in False Positives & Incident Response Time: Indicates improved threat detection without overwhelming security teams.
- Percentage of Data Classified and Encrypted: Measures coverage and adherence to policies.
- Audit Readiness Score & Compliance Status: Tracks alignment with regulatory mandates.
- Mean Time to Detect (MTTD) & Respond (MTTR): Measures operational efficiency and effectiveness of incident handling.
According to recent reports, organizations using AI-powered security systems in 2024 could detect and contain data breaches 108 days faster than others, leading to an average cost saving of $1.76 million per breach.Monitoring these metrics helps organizations evaluate AI security strategies and make informed improvements.
The Future of AI in Data Security
The AI landscape continues to evolve:
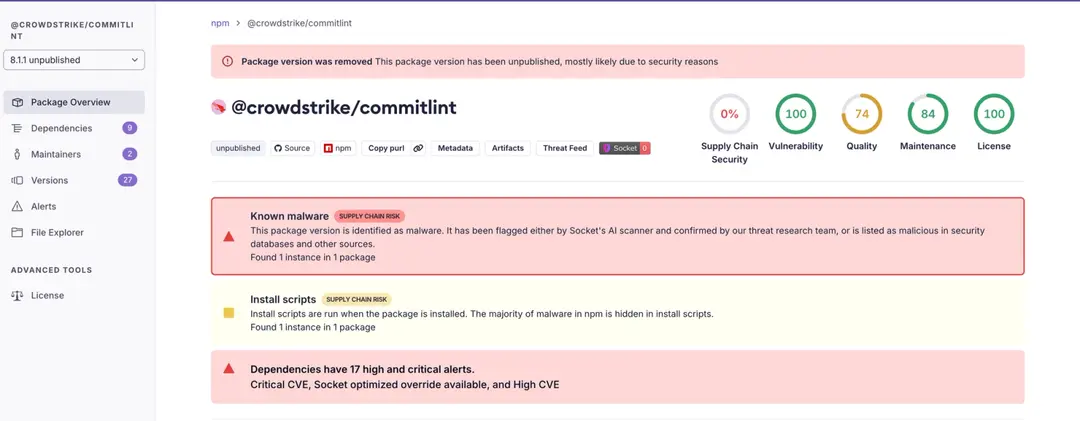
- Emerging Threats: Attackers will increasingly target AI pipelines and model integrity. For example, a recent Zenity Labs study shows AI agents are highly vulnerable to hijacking attacks.Security teams should track evolving tactics through resources like the AccuKnox Attack Research Database to stay ahead.
- Predictive Threat Intelligence: AI will anticipate attacks proactively, improving preventive measures.
- AI Governance and Regulatory Standards: Organizations will need to comply with new frameworks for safe AI deployment.
- Federated Learning & Secure Model Sharing: Collaborative training without sharing raw data will become a key privacy-preserving approach, supported by runtime security platforms like AccuKnox, which has a growing patent portfolio in areas including kernel instrumentation and runtime security.
By anticipating these trends, organizations can prepare to secure AI-driven operations for the long term.
Conclusion
AccuKnox offers a comprehensive solution for securing AI workloads, providing runtime enforcement, zero-trust controls, and AI Copilot insights. By integrating these tools, organizations can confidently leverage AI while protecting sensitive data and maintaining regulatory compliance.









